AWS Network Firewall for Egress and Ingress filtering
What is a Firewall?
A firewall is a system built to protect private networks from unauthorized and unverified access through an internet connection. Firewalls can be either in the form of hardware or software - or a combination of the two.
What is AWS Network Firewall?
AWS Network Firewall is a stateful, managed, network firewall and intrusion detection and prevention service for your virtual private cloud (VPC) that you created in Amazon Virtual Private Cloud (Amazon VPC).
With Network Firewall, you can filter traffic at the perimeter of our VPC. This includes filtering traffic going to and coming from an internet gateway, NAT gateway, or over VPN or AWS Direct Connect. Network Firewall uses the open source intrusion prevention system (IPS), Suricata, for stateful inspection. Network Firewall supports Suricata compatible rules.
AWS Network Firewall provides network traffic filtering protection for your Amazon Virtual Private Cloud VPCs. This tutorial provides steps for getting started with Network Firewall using the AWS Management Console.
Additionally, AWS Network Firewall provides extra features including deep packet inspection, application protocol detection, domain name filtering, and an intrusion prevention system. WAF, in contrast, can’t handle these features because it works on a different open systems intercommunication (OSI) model layer.
Enable Network Firewall
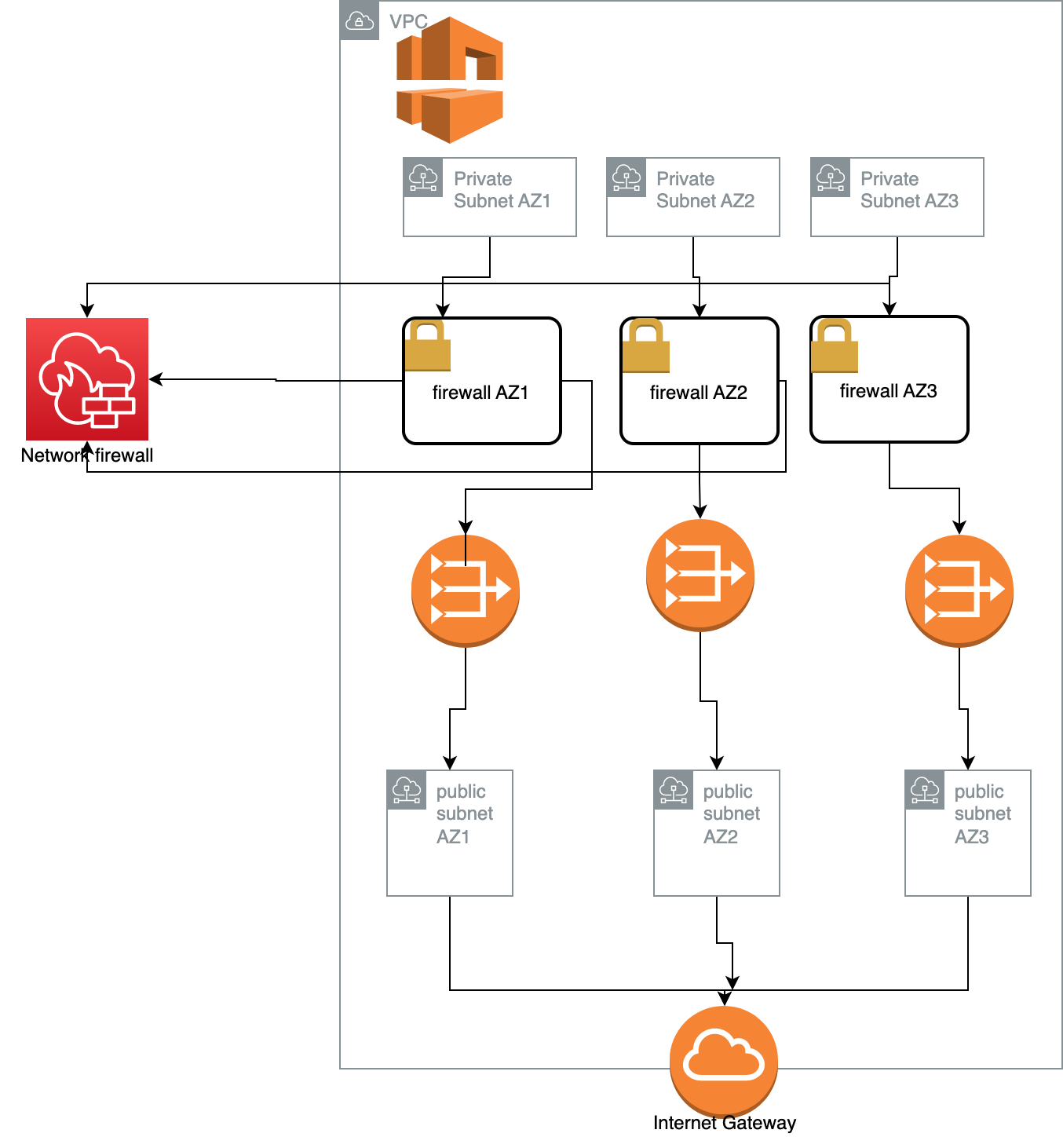
To enable the firewall’s protection, you modify your Amazon VPC route tables to send your network traffic through the Network Firewall firewall endpoints. For information about managing route tables for your VPC, see Route tables in the Amazon Virtual Private Cloud User Guide.
Components
- Rule group
- Firewall policy
- Firewall
Rule group – Holds a reusable collection of criteria for inspecting traffic and for handling packets and traffic flows that match the inspection criteria.
Firewall policy – Defines a reusable set of stateless and stateful rule groups, along with some policy-level behavior settings.
Firewall – Connects the inspection rules in the firewall policy to the VPC that the rules protect. Each firewall requires one firewall policy.
The AWS Network Firewall firewall runs stateless and stateful traffic inspection rules engines.
Implementing Network Firewall
To install and use an AWS Network Firewall firewall in AWS VPC, Firewall should directly be attached to subnet of the VPC. The Subnet egress and ingress traffic will be monitored and controlled. And all the traffic from the VPC will be redirected to the subnets using VPC endpoint.
- Configure the VPC subnets for your firewall endpoints
- Create the firewall
- Configure the firewall policy
- Modify VPC route tables to include the firewall
Firewall Behaviour
AWS Network Firewall provides virtual firewalls dedicated to protecting the VPC from attacks. We define and create a firewall, then use it to monitor and protect your subnets. The firewall monitors incoming and outgoing traffic and allows it to pass or drops it, according to the specifications. The firewall only allows packets to pass that pass inspection.
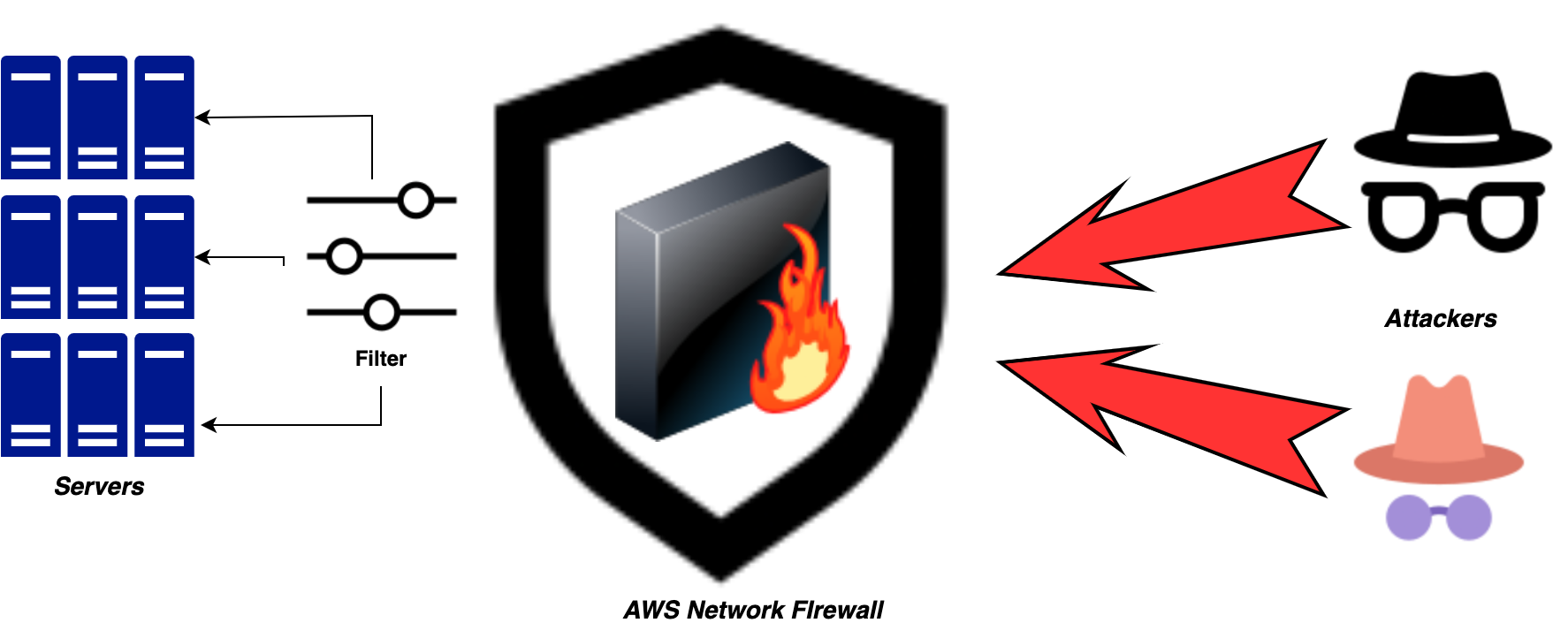
Network Firewall monitors and controls traffic to and from the protected subnets
Stateless and stateful rules engines
AWS Network Firewall uses two rules engines to inspect packets. The engines inspect packets according to the rules that you provide in your firewall policy.
-
Stateless rules engine - Inspects each packet in isolation, without regard to factors such as the direction of traffic, or whether the packet is part of an existing, approved connection. This engine prioritizes the speed of evaluation.
-
Stateful rules engine - Inspects packets in the context of their traffic flow, allows you to use more complex rules, and allows you to log network traffic and to log Network Firewall firewall alerts on traffic.
The stateful engine takes rules that are compatible with Suricata, an open source intrusion prevention system (IPS). Suricata provides a standard rule-based language for stateful network traffic inspection.
Network Firewall filters network traffic
When AWS Network Firewall inspects a packet, it evaluates the packet against the rules in the policy’s stateless rule groups first, using the stateless rules engine. Then, depending on that inspection and on other settings in the policy, it might evaluate the packets against the rules in the policy’s stateful rule groups, using the stateful rules engine.
-
Stateless rules engine - Network Firewall evaluates the rules in the order that they are prioritized in the rule group, starting from the lowest setting. We can create a stateless rule group, and set the priority of the rules in the rule group.
-
Default stateless rule actions - If a packet doesn’t match any stateless rule, Network Firewall performs the firewall policy’s default stateless rule action for full packet or UDP packet fragment, depending on the packet type. Network Firewall only applies the fragment action setting to UDP packet fragments, and silently drops packet fragments for other protocols.
-
Stateful rules engine - When Network Firewall forwards a packet to the stateful engine for inspection, it inspects each packet against the stateful rule groups, in the context of the packet’s traffic flow. You can configure a stateful rule to pass the packet through, with or without an alert, or drop it and send an alert.
Route table configurations
To include the firewall in the VPC, we have to modify the VPC route tables so that the traffic that we want the firewall to filter passes through the firewall endpoints.
Example format for Creating Rules using Suricata format
alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg:\".htpasswd access attempt\"; flow:to_server,established; content:\".htpasswd\"; nocase; sid:210503; rev:1;)